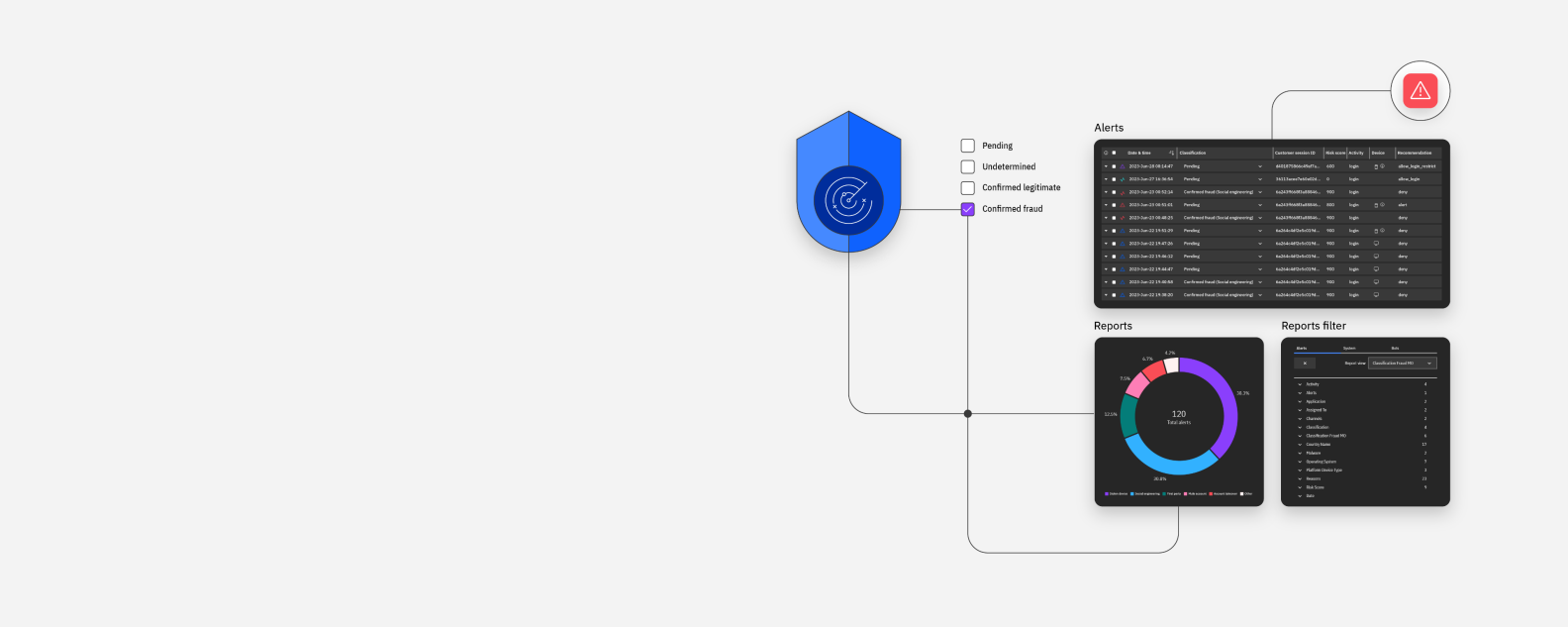
IBM Security® Trusteer® is a family of cloud services and endpoint device software that helps assess risk, detect fraud, establish identity and authenticate users. It is part of the IBM Security® portfolio.
IBM Security Trusteer solutions help you to detect fraud, authenticate users and establish identity trust across the omnichannel customer journey. Trusteer uses cloud-based intelligence, AI and machine learning to holistically identify new and existing customers while improving the user experience. Hundreds of leading organizations rely on Trusteer to help secure their customers’ digital journeys and support business growth.
In 2023, organizations saw a 71% spike in cyberattacks caused by exploiting identities. Check out the new report to learn how to best safeguard identities.
KuppingerCole Leadership Compass - See why Trusteer was named an overall leader in the latest Leadership Compass: Fraud Reduction Intelligence Platforms.
Outsmart account takeover attempts with AI, behavioral biometrics and machine learning.
Help power digital transformations by seamlessly assessing the risk of new and guest digital identities.
Enhance your mobile growth with real-time accurate device hygiene and session risk assessment.
Detect and remediate malware and identify phishing attacks.
156% ROI driven by Trusteer, as documented in the Forrester TEI report.¹
Greater than 90% fraud detection rate.
Less than 0.05% fraud alert rate.
Transparently identify unauthorized access and activities using advanced AI and machine learning.
Establish cross-organizational, actionable insights through real-time assessments.
Enable cross-channel coverage for mobile and web from account opening to existing user journeys.
Industry use cases
Faced with increased fraud attempts affecting the banking sector, BoursoBank armed itself with Trusteer to best protect its customers.
Banco Santander used Trusteer Rapport to help customers keep their details safe.
Forrester studied the ROI that enterprises may capture by deploying IBM Security Trusteer.
IBM Security Trusteer researchers discovered a new trend in financial mobile malware that targets Android and is replacing the classic overlay approach.
Regardless of your industry, delivering a frictionless customer experience across channels is key to digital growth.